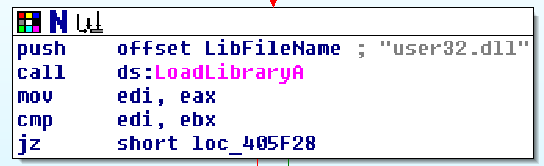
There are thousands of ways which makes malwares resist against static dissambling and static analysing. One of the known ways to circumvent against suspicious API blocking or analysing statically by AV’s, is using LoadLibrary API to dynamically load a library then use its functions and it makes a CPU Intensive task for AV’s to defeat this kind of malwares.

This technique consists of using functions like LoadLibraryA or VirtualAlloc then use GetProcAdress. As msdn says, GetProcAddress : Retrieves the address of an exported function or variable from the specified dynamic-link library (DLL).
So the viral routine just maps the dll in the process virtual space then finds the function which it needs from exported function the simply call the returned address from GetProcAddress. You can see a good example here.
But how can we analyse such a malware ? As you can imagine by now, there is no way to breakpoint on a function which was not loaded previously, in this case the windbg’s sxe comes to play. sxe triggers a breakpoint when a special dll loaded you can use it in the following way :
1
sxe ld:user32.dll
And another good option is execute command instead of just a simple breakpoint.
1
sxe -c "bp shell32!MessageBoxW" ld:user32.dll
This technique helps us to debug such viruses better and easier.
Comments powered by Disqus.